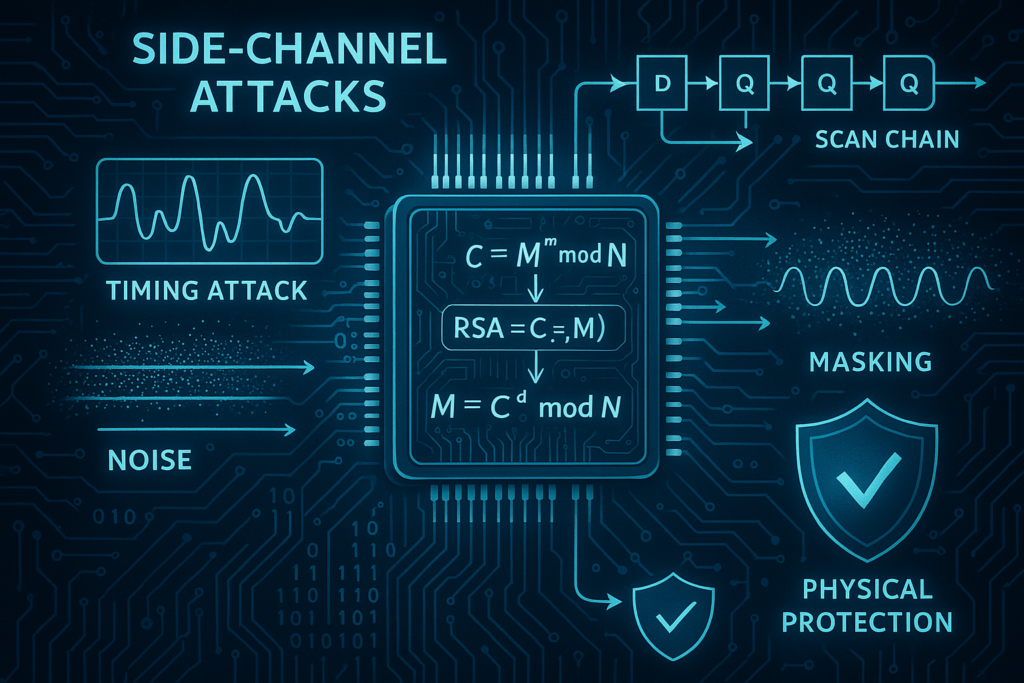
Unveiling Hardware Trojan Detection and the Design of Trusted Integrated Circuits
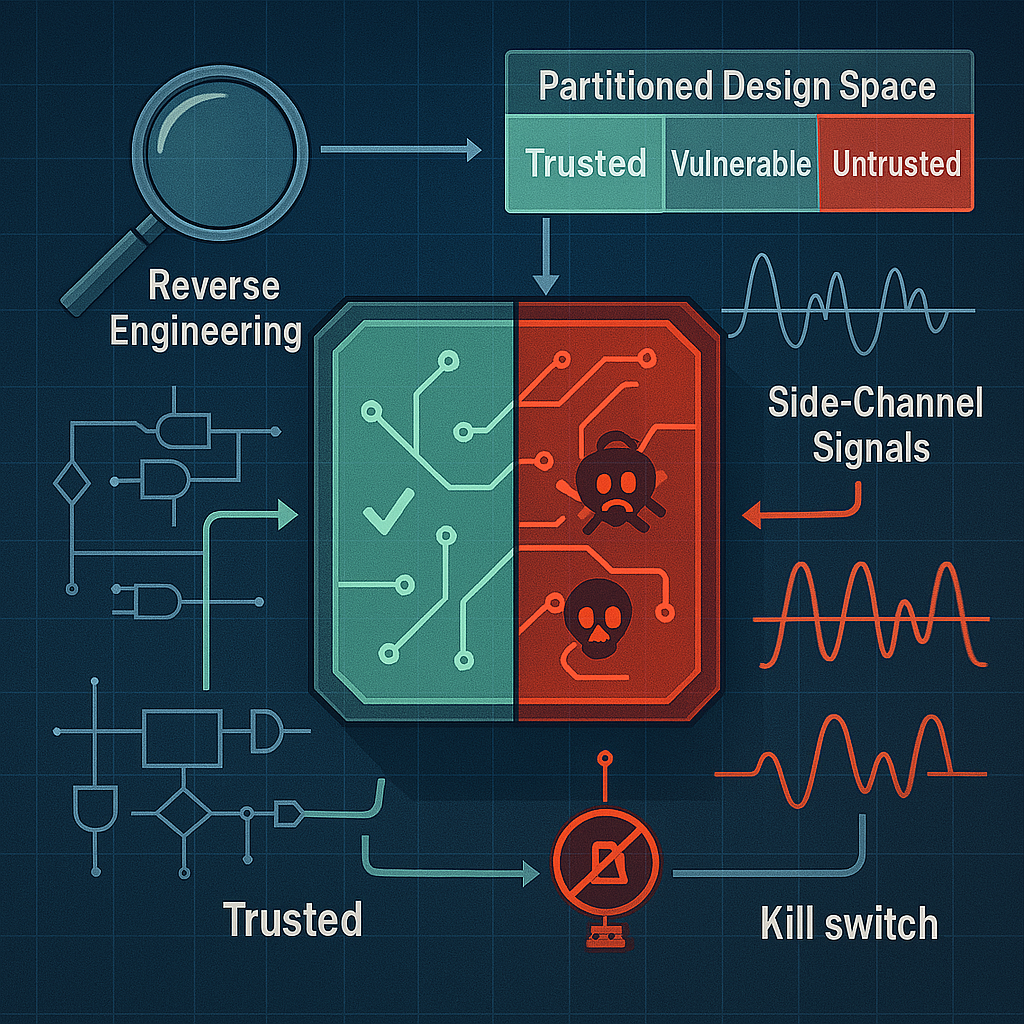
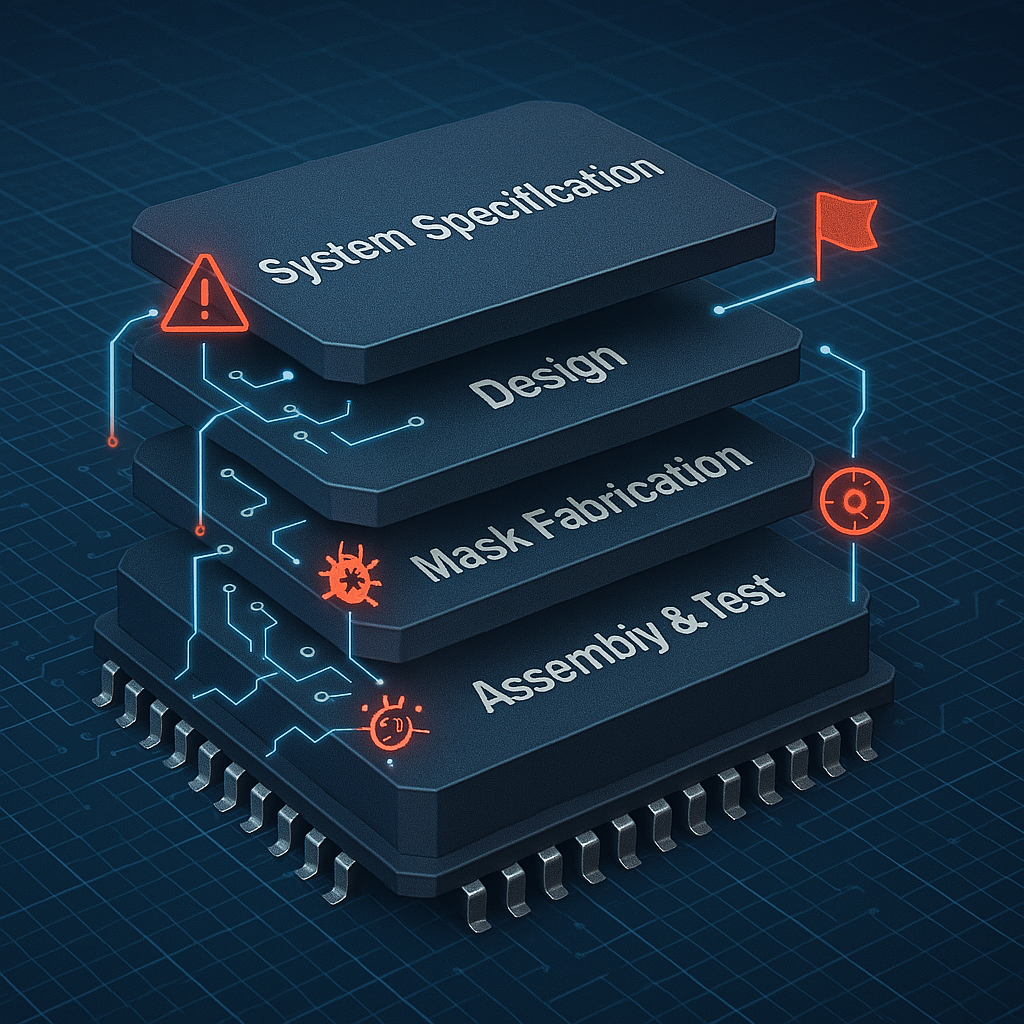
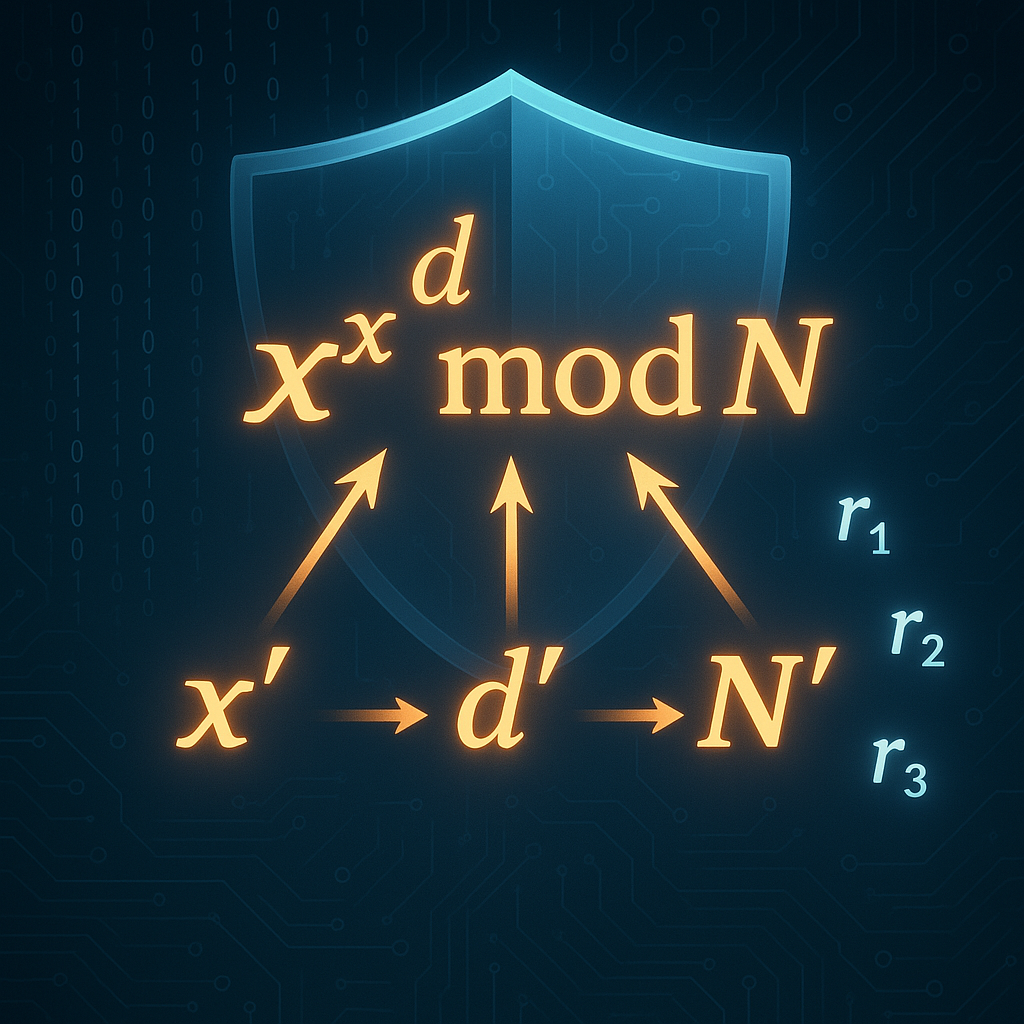
In the world of integrated circuits (ICs), ensuring the security and integrity of the design is one of the greatest challenges. In an environment where hardware Trojans—malicious modifications inserted into the hardware—can be added either intentionally or accidentally, understanding how to detect these threats is essential to ensuring system reliability. In this article, we explore […]