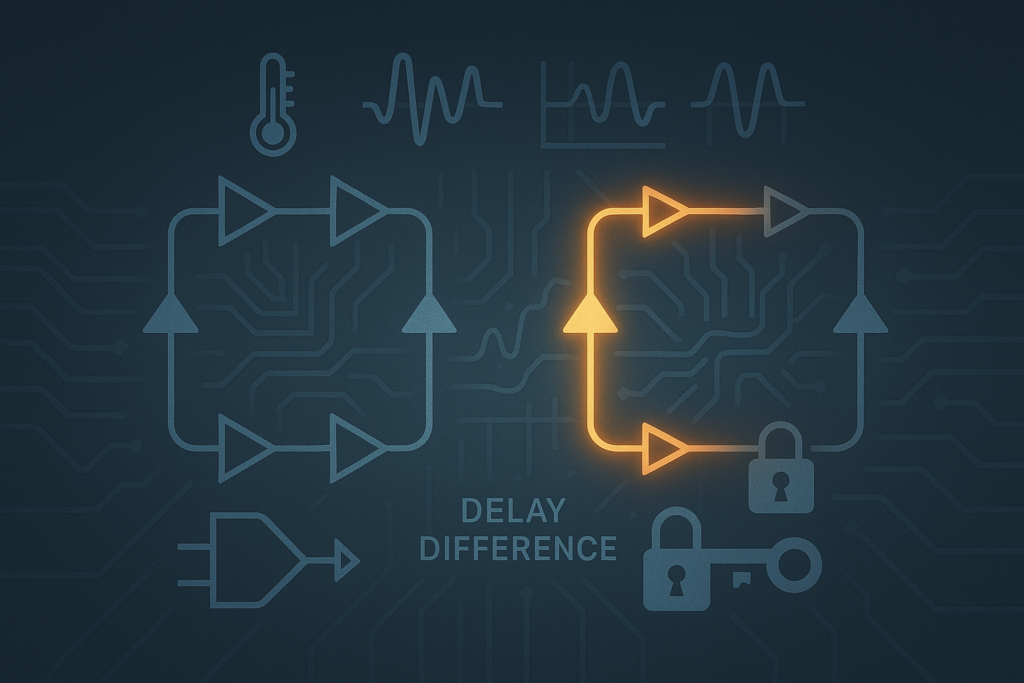
Reliability in PUFs: Unraveling the Challenges with Ring Oscillators
Digital security is constantly evolving, and to keep pace, innovative technologies like Physically Unclonable Functions (PUFs) are gaining prominence. Among the various types of PUFs, the Ring Oscillator PUF has emerged as a promising solution—but like any emerging technology, it still faces significant reliability challenges that must be overcome for high-security applications. What is a […]