In today’s world, where cyberattacks evolve daily, ensuring security in software development has never been more crucial. Integrating security practices into every phase of the Software Development Lifecycle (SDLC) not only protects data and systems but also contributes to the quality and robustness of applications. In this article, we will explore how to incorporate security from conception to operation, ensuring that software is developed securely and efficiently.
Understanding the Software Development Lifecycle
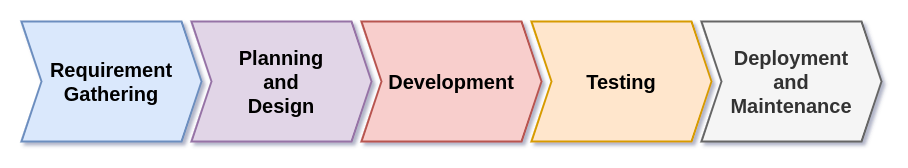
The SDLC is a structured process used to develop, test, and deploy software. While there are various versions – with phases ranging from five, six, or even twelve steps – the fundamental concepts remain the same:
- Requirement Gathering: Defining what the software must do and identifying functional and non-functional requirements.
- Planning and Design: Structuring the architecture, defining technologies, frameworks, and creating a design that meets both functional and security needs.
- Development: Coding the solution, implementing functionalities, and following secure coding practices.
- Testing: Verifying that the software meets requirements through manual and automated testing, as well as code reviews.
- Deployment and Maintenance: Putting the software into production and ensuring it is maintained and updated, fixing vulnerabilities, and managing changes.
By following a structured process, it is possible to avoid ad hoc development – the “just do whatever works” approach – which can result in security flaws and low-quality code.
Why Integrate Security into Every Phase?
Many developers prioritize functionality during development and consider security only at the end, as if it were a “seatbelt” to be fastened only after the car is in motion. However, this approach can lead to rework, increased costs, and, most importantly, critical vulnerabilities.
Integrating security into every SDLC phase offers several benefits:
- Risk Reduction: Identifying and mitigating risks early helps prevent major problems in later project stages.
- Compliance with Standards and Regulations: From the requirements phase, considering standards such as PCI DSS, NIST, OWASP Top 10, and MITRE CWE ensures compliance with security regulations in regulated industries.
- Cost-Effectiveness: Fixing vulnerabilities early in the development cycle is much more cost-effective than addressing them after the product launch.
- Improved Software Quality: Well-implemented security practices contribute to more robust code with fewer errors and easier maintenance.
Integrating Security into the SDLC Phases
1. Requirement Gathering and Planning
In this phase, it is essential to clearly define the software’s purpose and business expectations. To integrate security from the start, consider the following points:
- Risk Management: Identify potential risks and define strategies to mitigate them. Ask: “What could go wrong if this functionality is maliciously exploited?”
- Compliance Requirements: If the software operates in regulated sectors (such as finance or healthcare), it is crucial to include the security requirements mandated by specific regulations.
- Access and Privacy Policies: Establish which data will be collected, how it will be protected, and who will have access, applying the principles of confidentiality, integrity, and availability (CIA Triad).
2. Design and Architecture
During the design phase, the focus is on transforming requirements into an actionable plan that guides development. Key practices include:
- Threat Modeling: Analyze potential threats and vulnerabilities that could impact the system, enabling a resilient design against attacks.
- Attack Surface Evaluation: Identify which components and interfaces are most exposed to risks and define strategies to mitigate them.
- Principle of Least Privilege and Role Separation: Ensure that each software component has only the necessary permissions to perform its functions, minimizing exploitation risks.
- Defense-in-Depth Architecture: Implement multiple security layers so that, if one fails, other barriers can prevent full system compromise.
3. Development and Coding
During development, applying secure coding practices is crucial to transforming a robust design into a reliable product. Key considerations include:
- Secure Coding Practices: Follow recommended guidelines and standards to avoid common vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and buffer overflows.
- Dependency Management: Rigorously control libraries and frameworks used, regularly checking for updates or known vulnerabilities.
- Cohesion and Coupling: Develop components with high cohesion (well-defined functions) and low coupling (minimal dependencies between modules) to facilitate maintenance and security.
4. Testing and Validation
Testing software comprehensively is a crucial step to ensure all functionalities and security measures have been correctly implemented. Strategies include:
- Code Review: Conduct manual and automated reviews to identify potential security flaws and code improvements.
- Static and Dynamic Testing: Use tools to analyze the code (static testing) and simulate real-time attacks (dynamic testing or black-box testing) to detect vulnerabilities.
- Validation and Verification: Ensure that the software meets the defined requirements (verification) and actually solves the proposed problem (validation).
5. Deployment, Operation, and Maintenance
Even after launch, software security must be continuously monitored and improved:
- Change Management: Establish processes to manage updates and fixes, preventing the introduction of new vulnerabilities.
- Continuous Monitoring: Deploy monitoring tools that alert for suspicious activities and enable rapid incident detection.
- Incident Response Plan: Have a well-defined plan to respond to attacks, minimizing impacts and restoring normal operations as quickly as possible.
- Regular Updates and Patches: Keep the software up to date and fix vulnerabilities as soon as they are identified, preventing exploitation by attackers.
Supporting Frameworks and Tools
Several tools and frameworks can help integrate security throughout the SDLC:
- OWASP Top 10: Lists the ten most critical vulnerabilities in web applications, serving as a guide to avoiding major security flaws.
- MITRE CWE Top 25: Provides a ranking of the most critical vulnerabilities found in software, helping direct mitigation efforts.
- PCI DSS: A set of security requirements for organizations that process payment card data.
- NIST Framework: Offers comprehensive guidelines for implementing security practices in various contexts.
- DevSecOps: An approach that integrates security (Security) into development (Development) and operations (Operations), promoting a “security as code” culture.
Conclusion
Integrating security into every phase of the Software Development Lifecycle (SDLC) is essential to ensuring that applications are robust, reliable, and resilient to attacks. From requirements gathering to maintenance, security should be present as a vital component of the development process.
Adopting this approach not only protects data and a company’s reputation but also contributes to the creation of more efficient and sustainable software. By investing in integrated security practices and using recognized frameworks, organizations will be better prepared to face the challenges of today’s digital landscape.
Implementing a secure SDLC is a continuous investment that, in the long run, translates into resource savings and business peace of mind. Start reviewing your processes today and ensure that security is a priority in every line of code!
If you enjoyed this content and want to learn more about software security and best SDLC practices, keep following our blog for updates and essential tips to protect your projects.



Pingback: Security in Embedded Applications: Integrating SDLC for Secure Systems – FortShield: Cybersecurity and Embedded Linux
Pingback: Unveiling the Capability Maturity Model: How to Integrate It into the SDLC - FortShield: Cybersecurity and Embedded Linux
Pingback: Security in Software Development: Controls That Make a Difference - FortShield: Cybersecurity and Embedded Linux
Pingback: Source Code Security: How to Identify and Mitigate Critical Flaws - FortShield: Security for Professional Developers