Have you ever heard of SAMM in the context of software development? If not, get ready to discover an innovative approach that can transform the security of your projects. In this article, we will explore the Software Assurance Maturity Model (SAMM) in a clear and practical way, showing how it can help your team assess and improve security posture at every stage of development.
What is SAMM?
The SAMM (Software Assurance Maturity Model) is a framework that allows organizations to assess the maturity level of security in their development processes. Unlike other models that focus exclusively on processes or productivity, SAMM is entirely geared towards security – an area that can no longer be neglected today.
It provides a self-assessment to identify strengths and areas for improvement in the implementation of secure practices throughout the development lifecycle.
Why Integrate SAMM into Your Development Process?
Security is a critical aspect of any software, and SAMM was developed precisely to help teams:
- Continuously measure and improve the security of their systems.
- Identify gaps in the implementation of security practices.
- Increase software reliability, aligning it with business objectives.
- Implement consistent strategies that go beyond ad hoc efforts.
With SAMM, you not only check if your team is meeting the minimum requirements but also have a clear path to evolve and reach higher maturity levels.
Business Functions
SAMM v2 organizes software security into five main functions, each subdivided into specific practices that guide how security should be incorporated at each stage of development.
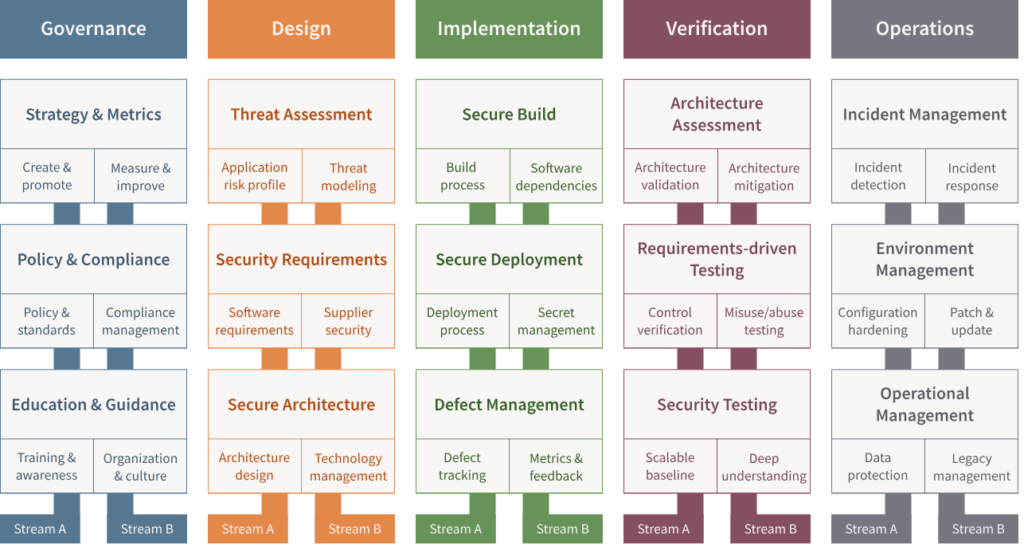
Below, we detail each of these functions and their components:
Governance
The Governance function is the foundation for organizational security, ensuring that strategies, policies, and internal culture align with security objectives. Its components are:
Strategy & Metrics
- Create & Promote: Develop and disseminate security strategies that clearly define objectives and expected standards. This includes creating guidelines that inform how security should be addressed across the organization.
- Measure & Improve: Establish metrics and indicators to monitor the effectiveness of security practices. This data-driven approach helps identify areas for improvement and implement corrective actions continuously.
Policy & Compliance
- Policy & Standards: Define and document security policies and standards that guide all areas of development and operations. These documents form the basis for best practices and serve as references for compliance.
- Compliance Management: Implement processes to ensure that all policies and standards are followed, both internally and by suppliers and partners. This includes regular audits and compliance assessments.
Education & Guidance
- Training & Awareness: Invest in continuous team training through workshops, awareness campaigns, and training sessions, ensuring that all employees understand security practices and their importance.
- Organization & Culture: Foster a security culture that permeates all levels of the organization, encouraging collaboration and knowledge-sharing about security across all areas.
Design
The Design function focuses on incorporating security early in the planning and architecture phase of software development. It aims to anticipate risks and structure solutions that minimize vulnerabilities:
Threat Assessment
- Application Risk Profile: Create risk profiles for applications, identifying which components and functionalities pose the greatest threat and require additional protection.
- Threat Modeling: Conduct threat modeling to map potential attacks and identify vulnerable points in the software architecture. This process helps prioritize efforts to mitigate the most critical risks.
Security Requirements
- Software Requirements: Define specific security requirements during the requirement gathering phase, ensuring that protection needs are considered from the start of development.
- Supplier Security: Assess and ensure that suppliers and partners providing components or services also comply with established security standards.
Secure Architecture
- Architecture Design: Design the system architecture with security in mind, incorporating standards and practices that prevent vulnerabilities and enable easy maintenance and scalability.
- Technology Management: Effectively manage the technologies used, ensuring they are up to date, compatible with security best practices, and can be securely integrated.
Implementation
The Implementation function addresses the practical execution of security guidelines during software development and deployment. This is where theory becomes practice:
Secure Build
- Build Process: Integrate security practices into the build process, ensuring that each compilation and continuous integration step includes security checks and validations.
- Software Dependencies: Manage and monitor software dependencies, ensuring that third-party libraries and components are free from known vulnerabilities and are regularly updated.
Secure Deployment
- Deployment Process: Develop and follow deployment processes that ensure the security of the environment where the software will be executed. This includes configuring isolated environments and adopting security best practices during deployment.
- Secret Management: Implement policies and tools for the secure management of secrets, such as API keys, passwords, and certificates, preventing unnecessary exposure and ensuring these data are adequately protected.
Defect Management
- Defect Tracking: Establish systems for tracking identified defects and vulnerabilities, allowing systematic monitoring and rapid resolution of security issues.
- Metrics & Feedback: Use metrics and continuous feedback to evaluate the effectiveness of implemented fixes and adjust development processes as needed, promoting continuous improvement.
Verification
The Verification function is responsible for validating whether security practices have been correctly implemented and ensuring that the software is protected against known threats. This stage involves a series of tests and evaluations:
Architecture Assessment
- Architecture Validation: Review the system architecture to ensure it meets established security requirements and that the implemented controls are effective.
- Architecture Mitigation: Identify and fix architectural flaws by implementing mitigation measures to reduce risks and improve system robustness.
Requirements-driven Testing
- Control Verification: Perform specific tests to validate whether the defined security controls function as expected and meet the requirements.
- Misuse/Abuse Testing: Test the software from an attacker’s perspective, identifying potential exploitation points and verifying whether defenses are strong enough to withstand abuse attempts.
Security Testing
- Scalable Baseline: Implement security tests that can be applied in a scalable manner across different software modules and versions, ensuring broad and consistent coverage.
- Deep Understanding: Conduct tests that go beyond the surface, deeply understanding the system’s behavior in attack scenarios and identifying complex vulnerabilities that could be exploited.
Operations
The Operations function focuses on maintaining security in production environments, ensuring that the software remains protected throughout its operational lifecycle. This includes active incident management and continuous maintenance:
Incident Management
- Incident Detection: Continuously monitor production environments to quickly identify any signs of incidents or anomalous behavior that may indicate an exploited vulnerability.
- Incident Response: Develop and practice incident response plans to ensure that the team is prepared to act quickly and mitigate the impact of a potential attack.
Environment Management
- Configuration Hardening: Apply configuration hardening techniques to reduce the attack surface, eliminating insecure settings and ensuring that systems are protected against known threats.
- Patch & Update: Keep the environment updated with patches and security updates, ensuring that known vulnerabilities are fixed before they can be exploited.
Operational Management
- Data Protection: Implement strict measures to protect data both at rest and in transit, ensuring that sensitive information is always safeguarded against unauthorized access.
- Legacy Management: Securely manage legacy systems by integrating them with modern security practices or planning their replacement to minimize the risks associated with outdated technologies.
Each of these functions plays a vital role in creating a robust and integrated security approach, where all development and operational processes are continuously assessed and improved. By following this structure, your organization will be better equipped to face modern security challenges in software development.
Maturity Levels
SAMM proposes a three-level structure to measure the progress and efficiency of security practices implemented in each development function. This segmentation allows organizations not only to understand their current position but also to outline a clear path for continuous improvement. Below is a detailed explanation of each level:
Level 1 – Basic or Initial
Objective:
Establish the minimum necessary to ensure that security is considered during development.
Characteristics:
- Ad hoc practices: Security actions are carried out reactively and in an unstructured manner. There may be isolated initiatives, but without planning or standardization.
- Lack of consistent documentation: Processes and procedures may not be formally documented, making replication or systematic improvement difficult.
- Fragmented knowledge: The team has knowledge of security, but its application varies significantly between members and projects.
Indicators:
Adoption of some basic measures, such as input validation or occasional code reviews, without an integrated security strategy.
Level 2 – Intermediate or Managed
Objective:
Move from a reactive approach to a more structured and consistent methodology in the application of security practices.
Characteristics:
- Standardized processes: Security practices begin to be formalized and documented. Processes and checklists are created to guide the team more uniformly.
- Monitoring and metrics: The organization starts measuring the effectiveness of security actions. There are metrics and indicators that allow performance evaluation and identification of improvement points.
- Continuous training: There is a conscious effort to train the team with regular sessions, ensuring that security standards are understood and followed by all.
- Integration with development processes: Security is incorporated into the development cycle, for example, through systematic code reviews and security testing.
Indicators:
A more proactive approach, with evidence that practices are being monitored and adjusted as necessary, increasing the reliability of systems.
Level 3 – Advanced or Optimized
Objective:
Achieve security excellence by integrating it continuously and strategically into all development processes.
Characteristics:
- Continuous improvement: The organization adopts a robust feedback and learning cycle, using post-incident analyses and regular reviews to enhance security practices.
- Automation and deep integration: Automation tools and integrated processes enable early vulnerability detection and immediate incident response, minimizing risks.
- Consolidated security culture: Security becomes an intrinsic part of the organizational culture. All hierarchical levels are engaged, from top management to developers, ensuring a holistic and committed vision.
- Innovation and adaptation: The organization not only follows industry best practices but also invests in research and innovation to adapt to new threats and challenges in the technological landscape.
Indicators:
Evidence of integrated and adaptive security, with optimized processes that not only prevent incidents but also foster innovation and continuous improvement. Internal and external audits demonstrate high compliance and effectiveness of the implemented measures.
By clearly defining these maturity levels, SAMM provides a roadmap for companies to accurately self-assess and identify which areas require greater investment and attention. This structure not only facilitates strategic planning but also enables clear communication with stakeholders regarding the current state and future objectives of security in software development.
How to Implement SAMM in Practice
Integrating SAMM into your workflow may seem challenging at first, but some tips can make this process easier:
1. Conduct a Self-Assessment
Self-assessment is the first and most crucial step for a successful SAMM implementation. This process involves a detailed and honest analysis of where your organization stands in terms of security. Here’s how to delve deeper into this stage:
- Mapping Processes and Functions:
Identify and document all business functions related to software development – such as governance, design, implementation, verification, and operations. Understand how each of these areas currently integrates security practices. - Evaluation of Security Practices:
For each function, analyze existing security practices, such as strategy and metrics, policy and compliance, and education and guidance. Use questionnaires, team member interviews, and document reviews to identify strengths and gaps. Ask yourself, for example:- Are security metrics being consistently collected and analyzed?
- Are security policies regularly reviewed and communicated to all employees?
- Is there adequate training to keep the team updated on best practices?
- Current Maturity Analysis:
Compare the current situation with the three maturity levels proposed by SAMM. Determine whether each area is at the basic level (minimum required), intermediate (structured processes), or advanced (continuously improved practices). This comparison will help define where your organization needs to evolve. - Data Collection and Indicators:
Gather quantitative and qualitative data that can serve as a basis for evaluation. This may include incident records, security audit results, team feedback, and performance metrics. These indicators are essential for measuring progress and setting future goals. - Risk and Priority Identification:
Use the self-assessment results to identify the most critical risks and areas requiring immediate attention. Prioritize improvement actions based on their potential impact on software security and the organization’s strategic objectives.
This step not only provides a detailed diagnosis of the current state but also serves as a starting point for defining a robust action plan. By thoroughly understanding your current position, you can chart a clear path to sustainably progress toward higher levels of security maturity.
2. Set Realistic Goals
When implementing SAMM, it is essential not only to diagnose the current situation but also to establish improvement objectives that are feasible and measurable. To begin, map the current maturity level of each security practice identified in the self-assessment. Identify which areas are at Level 1 and where there is potential for evolution to Level 2 or even Level 3.
Use concrete data, such as the frequency of security control updates, the rate of detected incidents, and the effectiveness of responses to these incidents, to support your goals. Break these goals into short-, medium-, and long-term steps, defining clear milestones and periodic reviews. This incremental approach allows the team to see tangible progress while adjusting the strategy as needed.
It is also essential to involve all stakeholders in defining these goals, ensuring that they align with business objectives and that everyone involved commits to the continuous improvement process. This way, the goals will not only be ambitious but also realistic and achievable, serving as a guide for consistent security enhancement throughout all phases of development.
3. Empower Your Team
Empowering your team goes far beyond just offering basic training. It is essential to invest in continuous education programs and an environment that encourages collaborative learning. Here are some detailed strategies to strengthen your team’s security skills:
- Specific Technical Training: Organize workshops, courses, and certifications focused on security practices and the use of tools recommended by SAMM. These trainings should cover everything from basic security concepts to advanced topics such as vulnerability detection and incident response. This ensures that developers, testers, and managers understand the nuances of each practice and can apply this knowledge daily.
- Update and Refresher Sessions: The threat landscape evolves rapidly. Therefore, it is important to schedule regular update sessions where the team can discuss new trends, emerging vulnerabilities, and best market practices. These sessions can be conducted through webinars, internal lectures, or partnerships with external experts.
- Collaborative Learning Environment: Encourage knowledge sharing within the team through periodic meetings, discussion forums, and working groups. Collaborative platforms such as internal wikis or dedicated communication channels allow members to share experiences and solutions to common problems, reinforcing the security culture.
- Simulations and Practical Exercises: Theory is essential, but practice consolidates learning. Conduct security incident simulations and crisis response exercises so that the team can test and refine its protocols. These exercises help identify weaknesses in processes and create realistic action plans for emergency situations.
- Incentives and Recognition: Recognize and reward individual and collective efforts in improving security practices. Incentives can range from internal certifications to awards that motivate the team to engage even more in security initiatives.
By adopting these strategies, you not only empower your team but also create a robust and proactive security culture, which is fundamental to successfully implementing SAMM and protecting your software assets.
4. Use Online Tools and Resources
Taking advantage of tools and resources available on the internet can accelerate the implementation of SAMM and ensure that you are following the best security practices. Various platforms and materials can complement the use of the model:
- Official Websites and Documentation: OWASP, for example, offers a dedicated SAMM page where you can find detailed documentation, step-by-step guides, and even templates to assist in self-assessment. These resources provide an in-depth view of each practice and maturity level, explaining how to implement corrective measures and monitor security evolution.
- Interactive Tools and Dashboards: Some online tools allow you to perform interactive self-assessments by filling out forms that generate visual dashboards of your maturity level. These dashboards make it easier to visualize strengths and areas that need improvement, allowing you to track progress over time.
- Communities and Discussion Forums: Participating in communities such as forums, LinkedIn groups, or Slack channels dedicated to information security and SAMM can be extremely useful. On these platforms, professionals share experiences, tips, and even challenges faced in implementing the model, which can help identify solutions to common problems.
- Webinars and Online Courses: Many institutions and experts offer webinars, courses, and workshops focused on SAMM and secure software development. These online events are great opportunities to learn about the latest trends, gain practical insights, and even ask questions directly to experts.
- Automation Tools: There are also automation tools that integrate SAMM with other security and development solutions. They help continuously monitor the performance of security practices, automating data collection and report generation, making it easier to identify areas that need attention.
By combining these resources, your team can not only better understand SAMM but also apply it more effectively, ensuring that security remains up to date in all phases of development.
5. Continuously Monitor and Review
Security is not a one-time setup – it needs to be continuously monitored and adjusted to address new threats and challenges. To do this, it is crucial to establish robust monitoring and review processes. Here are some detailed steps to ensure this practice is effective:
- Implementation of Monitoring Tools: Use security monitoring and analysis solutions such as intrusion detection systems (IDS), security information and event management (SIEM), and vulnerability analysis tools. These tools help identify incidents in real-time and provide detailed reports on security health in your environment.
- Definition of Key Performance Indicators (KPIs): Establish clear metrics to assess the effectiveness of security practices. For example, set goals for incident response time, the number of identified and corrected vulnerabilities, or the frequency of penetration testing. These indicators provide an objective view of performance and help direct improvement efforts.
- Periodic Reviews and Audits: Schedule regular reviews of security processes and practices. Conduct internal audits and, if possible, hire external specialists for an independent analysis. These audits can reveal blind spots and provide valuable insights for continuous improvement.
- Feedback and Process Updates: Create a feedback cycle that involves the entire team. Gather information from security incidents, lessons learned, and team suggestions to adjust policies and processes. Document these changes and ensure that all members are aware of the new guidelines.
- Incident Tests and Simulations: Conduct incident simulation exercises to evaluate your team’s response capacity. These tests help identify failures and train the team to respond quickly to real situations, ensuring that detection and response processes are well-tuned.
By adopting a systematic approach to monitoring and reviewing, your organization not only reacts to incidents but anticipates them, continuously improving its security posture. This ongoing practice is essential to maintaining the effectiveness of implemented strategies and adapting to the constant evolutions in the threat landscape.
Benefits and Challenges of Implementation
Benefits
- Complete visibility: Understand exactly where your security needs improvement.
- Alignment with business objectives: Security ceases to be an isolated item and becomes an integral part of the company’s strategy.
- Continuous improvement: A model that encourages constant evolution, preventing vulnerabilities and strengthening customer trust.
Challenges
- Initial complexity: The SAMM framework may seem complex, but with good planning and training, it becomes more intuitive.
- Cultural change: Adopting SAMM requires the team to adopt a mindset of continuous improvement and shared responsibility regarding security.
Extra Tips to Boost Your Security Strategy
- Detailed Documentation: Keep clear records of security practices and maturity level developments. This facilitates audits and demonstrates the team’s commitment.
- Open Communication: Encourage the sharing of ideas and experiences among team members to promote a security culture.
- Constant Updates: The threat landscape is always evolving. Stay updated with best practices and new tools available in the market.
Conclusion
Integrating SAMM into software development is a powerful strategy to ensure security is present at every stage of your project. By adopting this model, your team not only evaluates the current stage but also has a clear roadmap to evolve and align with business objectives. With well-defined practices, maturity levels, and a constant focus on improvement, SAMM can be the differentiator that makes your software more reliable and secure.
We hope this guide has clarified what SAMM is and how you can start implementing it in your organization. Remember: security is not a destination, but a continuous journey of improvement. Good luck and get to work!


