In the world of integrated circuits (ICs), ensuring the security and integrity of the design is one of the greatest challenges. In an environment where hardware Trojans—malicious modifications inserted into the hardware—can be added either intentionally or accidentally, understanding how to detect these threats is essential to ensuring system reliability. In this article, we explore the concepts and challenges of hardware Trojan detection and its relationship with the design of trusted ICs in a fluid and engaging style.
What Are Hardware Trojans?
Hardware Trojans are malicious or unwanted modifications introduced into an integrated circuit that can compromise its functionality or leak sensitive information. These “invaders” can range from large blocks of circuitry with specific functions to minor tweaks, such as a simple logic gate acting as a “kill switch.” The main idea is that once activated, these elements can disable functionalities, reduce system reliability, or breach data security.
The Relationship Between Hardware Trojan Detection and Trusted Design
For a fabricated IC, the goal of hardware Trojan detection is to determine whether the chip contains any malicious elements and, consequently, whether it can be considered trustworthy. However, it is important to note that not detecting a Trojan does not guarantee 100% security. Even a circuit that appears flawless may have vulnerabilities—both functional and parametric—that can compromise its performance in the long run.
Evaluating System Trustworthiness
When evaluating the reliability of a circuit, the design space is divided into several regions:
- Successful Designs: Meet all specifications.
- Failed Designs: Do not meet certain requirements.
- Designs with Malicious Functionality: These may or may not be detected by security algorithms.
- “Innocent” Designs: Even though they don’t exhibit malicious behavior, they still fail to meet some specifications.
This categorization helps classify circuits as either “trusted” or “untrusted,” allowing engineers to identify which designs can be safely used.
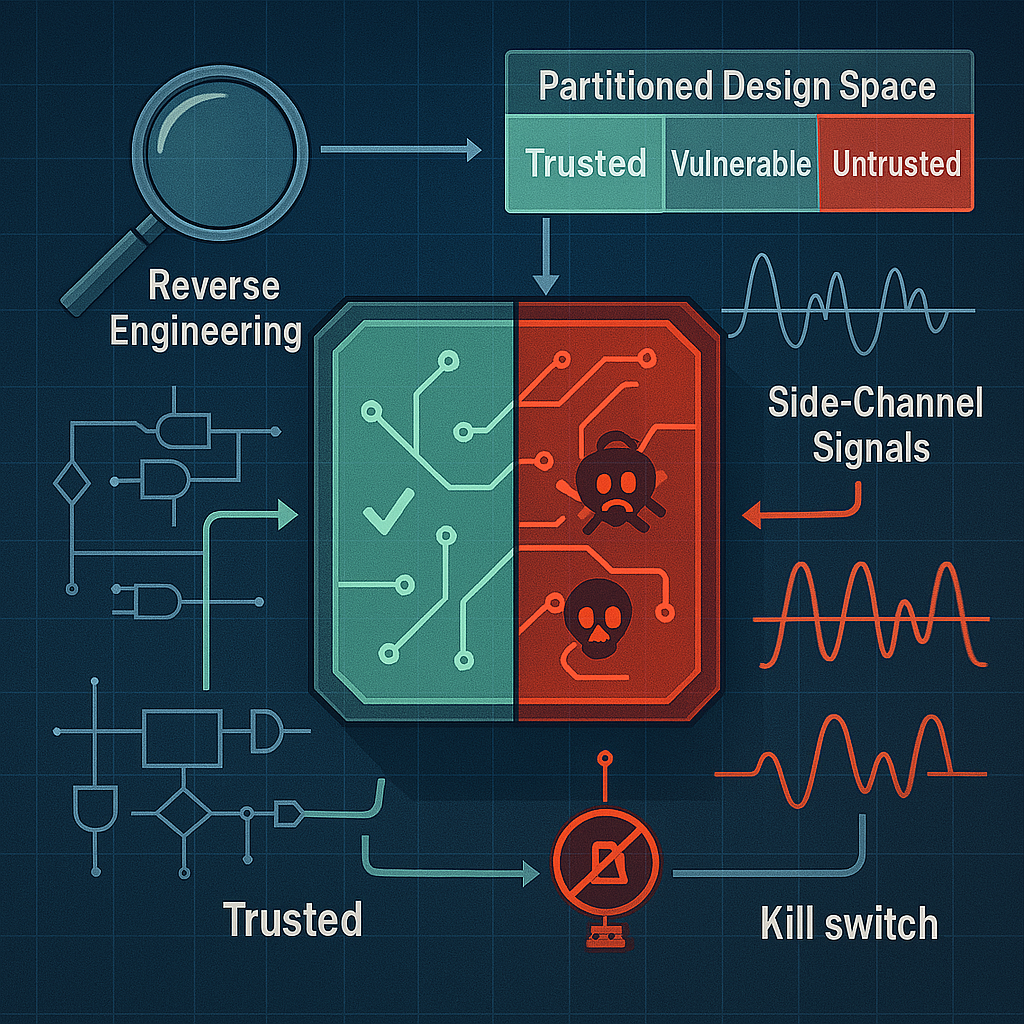
Challenges in Detecting Hardware Trojans
Detecting hardware Trojans is a complex challenge for several reasons:
- Variety of Implementations: Trojans can be inserted in various forms, from significant additions to nearly imperceptible modifications.
- Hidden Locations: They can be embedded in various parts of the system, such as memory, I/O devices, or processors.
- “Silent” Mode: Many remain inactive until triggered, making them difficult to detect during conventional testing.
- Noise and Manufacturing Variations: Measurement errors, manufacturing variations, and inherent “functional noise” can make it hard to distinguish between accidental faults and malicious modifications.
Moreover, traditional testing and verification methods are designed to identify manufacturing defects, not intentional malicious modifications.
Approaches to Detecting Hardware Trojans
There are primarily two approaches for identifying hardware Trojans:
1. Destructive Approach
This technique involves removing the chip’s package to expose the die and conducting a detailed reverse engineering analysis. Although this approach can accurately reveal any malicious modifications, it is extremely expensive, requires sophisticated equipment, and may not be practical for analyzing every fabricated chip.
2. Non-Destructive Approaches
Among these, two main methods stand out:
- Run-Time Monitoring: Continuously monitors control signals and the input-output relationships of critical system blocks to detect any anomalous behavior that could indicate a Trojan.
- Side-Channel Analysis: Utilizes physical measurements such as power consumption and electromagnetic emissions to identify small variations that may be attributed to a hardware Trojan. While promising, this method can be affected by noise and natural manufacturing variations.
In both cases, the goal is to build a level of trust in the design that allows for the identification and mitigation of potential threats, even if it is impossible to claim with absolute certainty that the circuit is entirely secure.
The Impact of Physical Attacks and the Attacker’s Strategy
Physical attacks, such as reverse engineering and side-channel analysis, are powerful techniques used by both attackers and detection mechanisms. When a chip is subjected to a physical attack, the attacker may remove layers of the device to map its internal structure and identify vulnerable points.
Conversely, hardware Trojan designers aim to insert malware that is both:
- Effective: Capable of being triggered at the right moment to cause significant damage.
- Stealthy: Designed to go unnoticed by conventional testing or side-channel analysis.
A clear example is the “kill switch,” which must be activated in a controlled manner without visibly altering the original design. To mitigate this risk, detection systems must monitor not only control signals but also side channels and operating conditions.
Strategies to Minimize Risks and Ensure Security
Given the challenges presented, several strategies can be adopted to improve circuit reliability:
- Implementing Multiple Layers of Security: Combining side-channel analysis, real-time monitoring, and formal verification of control signals can reduce the probability of both false negatives and false positives.
- Continuous Monitoring: In critical systems, constant monitoring of signals and chip operations can help detect abnormal behavior indicative of a Trojan.
- Strict Control of External Components: Ensuring the integrity of external connections and wireless signals associated with the chip can prevent attackers from triggering malicious mechanisms like a kill switch.
- Third-Party Component Evaluation: Since Trojans can be introduced via untrusted design tools or third-party IPs, rigorous validation of each component is essential to maintain a high level of trust.
Conclusion
Hardware Trojan detection and the design of trusted integrated circuits are complex challenges that require a multifaceted approach. Although it is impossible to guarantee 100% security, combining destructive testing, real-time monitoring, and side-channel analysis significantly enhances system trustworthiness. With the advancement of detection techniques and continuous development of protective methods, the semiconductor industry is moving toward designs that are increasingly secure and robust.
Understanding the nuances and challenges of hardware Trojans enables engineers and security professionals to develop more effective strategies for protecting critical systems, ensuring that devices perform exactly as expected—without any malicious surprises.
Related Articles
To further explore topics related to hardware Trojan detection and trusted integrated circuits, check out the following articles:
- “Hardware Trojan Taxonomy: Understanding the Hidden Threats in Chips”: Dive into the classification of hardware Trojans, their triggers, payloads, and the challenges they pose to chip security.
- “Side-Channel Attacks: Exploring Vulnerabilities in Modern Cryptography”: Learn how side-channel analysis techniques, such as power and electromagnetic measurements, can be used to detect or exploit hardware vulnerabilities.
- “Physical Attacks on Hardware: Unveiling Threats and Defense Strategies”: Discover practical strategies to defend against physical attacks and ensure hardware reliability.
- “Power Analysis Attacks: Unveiling SPA and DPA in Cryptographic Security”: Understand how power analysis attacks work and explore countermeasures to protect cryptographic systems.
These articles provide a comprehensive view of hardware security, offering insights into detecting and mitigating vulnerabilities in integrated circuits.





