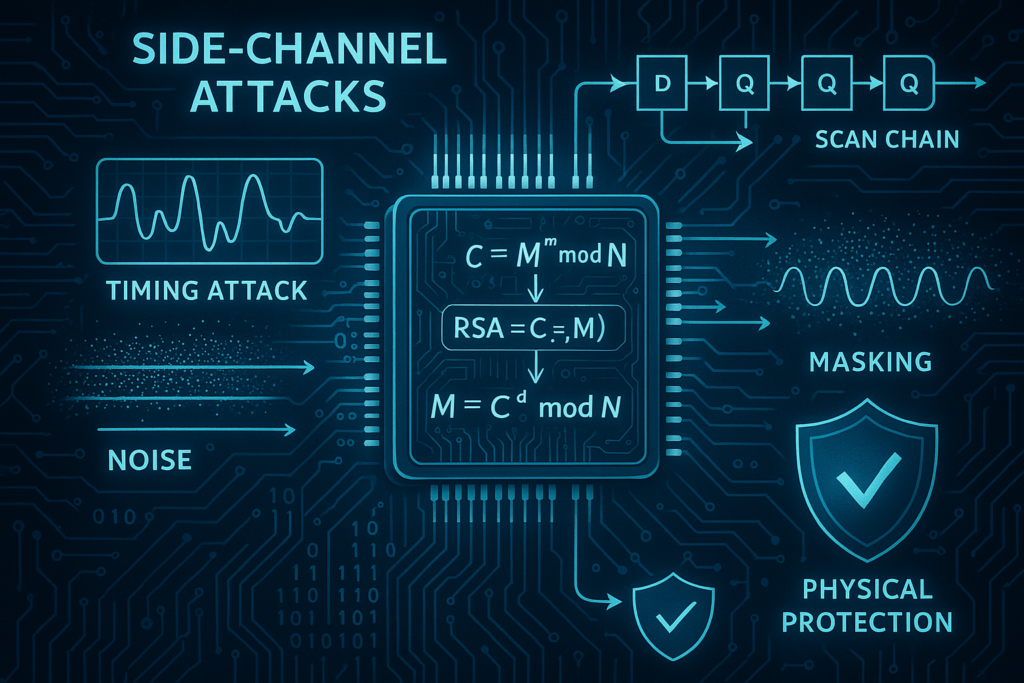
Unveiling Side Channel Attacks: Timing and Scan Chain Techniques
The security of cryptographic systems is an ever-evolving subject, and the methods used to attack them are continuously improving. Among the various types of side channel attacks, timing attacks and scan chain attacks stand out as particularly sophisticated threats. In this article, we explore how these attacks work using the RSA algorithm as an example, […]